Ok I signed up for VIP. Why? Because I didn’t realize that I needed VIP to send my CPE’s in for the machines I’ve owned. RIP.
SwagShop
Enumeration:
I decided to try and hack this machine. I have no idea what’s on it. I started my nmap $TARGET_IP -T4 , I’m trying to see if there’s any common ports, then if nothing significant shows up, I’ll do a more in-depth scan with nmap $TARGET_IP -p- -sC -T4 break down:
-p- means scan all ports
-sC means to run default scripts against the selected ports (in this case all of them)
-T4 means aggressive scan
With the initial scan, I got two ports open:
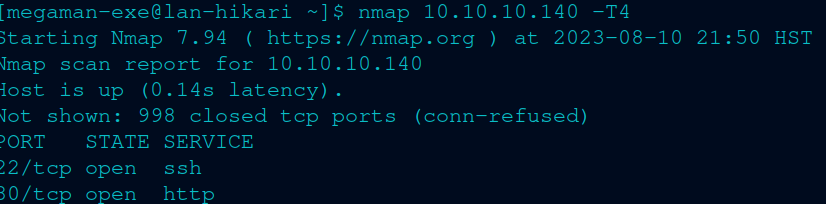
So I’ll run a service scan or -sV and – sC (you never know, sometimes, new things will pop up with the -sC scan) on the two ports, and then check out the http server. While I check out the http server, I’ll run the aggressive scan like I mentioned. Here’s the scan:
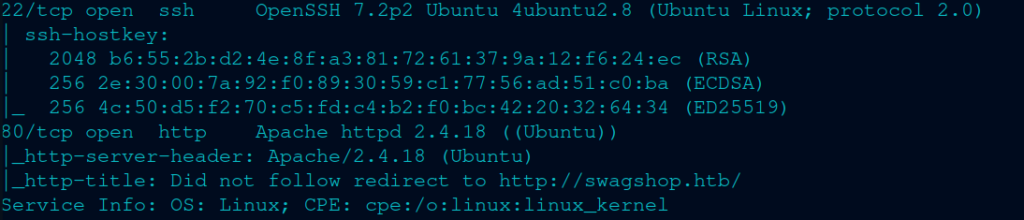
From what I’m reading here is that it’s using a openssh server (which I think is secure) then an apache 2.4.18, which I’m not sure about, so I’ll have to do some CVE research if I don’t find anything in the webpage. Anyways, I have to add the IP address to my /etc/hosts file to do anything further. Here’s a quick way to do it without vim/nano:
So I’m starting my aggressive scan, and looking through the webpage. Ok just kidding, I forgot that I can use the –script http-enum. The command looks like this:
nmap $TARGET_IP -p 80 --script http-enum
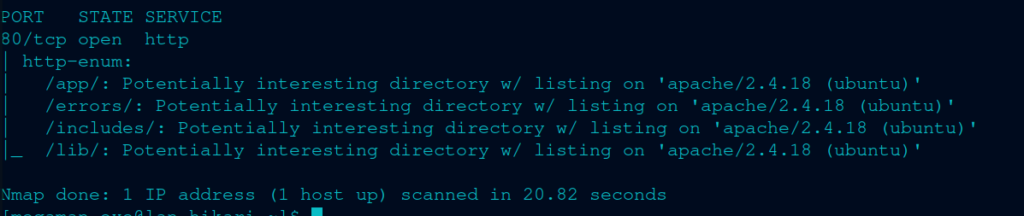
I couldn’t find anything alarming while going through the site. So I looked for the CVE vulnerabilities.
I couldn’t really find anything that would allow remote code execution.But I realized when I tried http://swagshop.htb/includes/ that it allowed directory traversal, at least within the website directory.
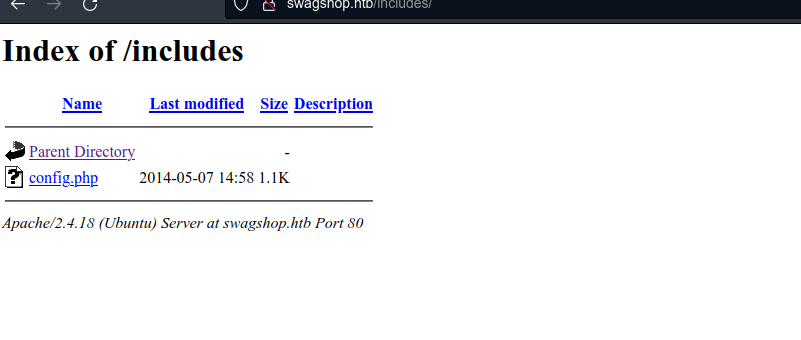
I’ll do some more snooping here.
Ok I did a lot of research. I actually researched a lot about Magento, which is what this target is hosted off of. Basically it’s the WordPress version of Adobe, and there’s a lot of exploits. One in particular, allows remote code execution. CVE 2022-24086, there’s a couple of proof of concepts, but I can’t actually find how it’s executed. It implies that it’s executable in the cart checkout area, but there’s no photos or further explanation. Maybe there is, and I can’t find it. Anyways, maybe I’ll further test it, but I also found out that searchsploit is an available tool for OSCP and I’ll check that out as well.
Ok – here’s my searchsploit for Magento:
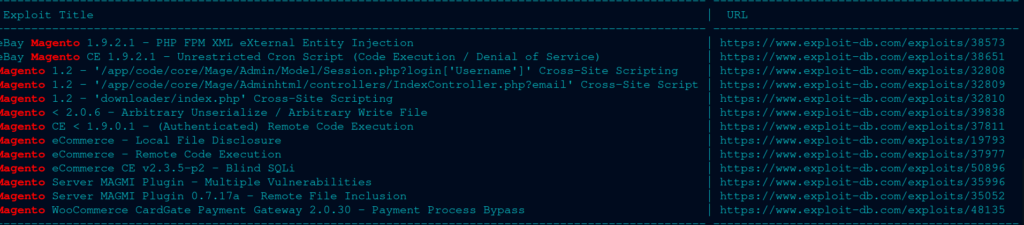
I’m specifically looking for a RCE or remote code execution. This is so that I can pass a shell and I can get the user flag. So there definitely is one, and documentation of the script here: https://www.exploit-db.com/exploits/37977
Wait… there’s a payment gateway bypass… what the heck. Ok – well, that’s interesting.
I’m going to try and execute the 37977.py code.
Ok… it says it did not work. I’m going through the code, and I think the admin path is incorrect, but I don’t know where it could be.
Ok… looks like I’m having trouble running the code because it’s an old version of python. I’m going to abandon this. I tried making a curl of the the same POST, but I’m too tired to make sense of the python code right now. Maybe I’ll update this later.
